Features
Align your security strategy with what actually matters.
Secure Origin provides a continuous validation layer that identifies detection gaps, prioritizes real risk, and preserves control of your security data—without forcing costly rip-and-replace decisions.
Enterprise-grade security
Without enterprise overhead.
Secure Origin complements SIEMs, scanners, and MDRs by validating what actually works—so teams can prioritize with confidence.
Data Sovereignty
Maintain ownership and control of your security data. Secure Origin deploys dedicated infrastructure while ensuring customers retain control over access, retention, and portability.
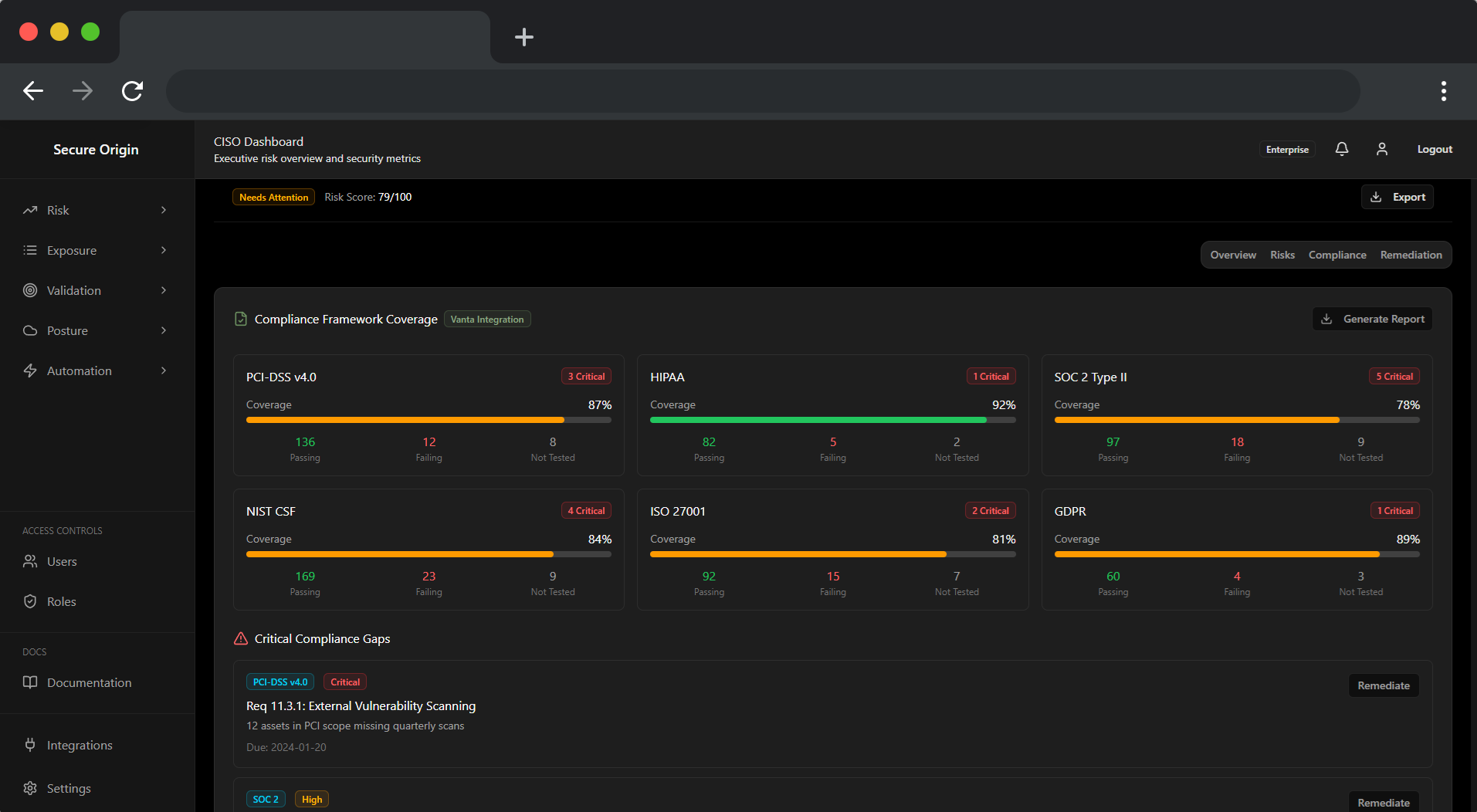
The Risk Brain
Technical findings are translated into business-relevant risk, ranking exposures based on asset criticality, identity context, and potential impact to your most important systems.
Measurable ROI
Track improvement using metrics like Mean Detection Gap, which help quantify how detection coverage and control effectiveness improve over time.
Transform your security foundation without disruption.
Designed to support the full CTEM lifecycle
From discovery and prioritization to validation and response.
From discovery and prioritization to validation and response.
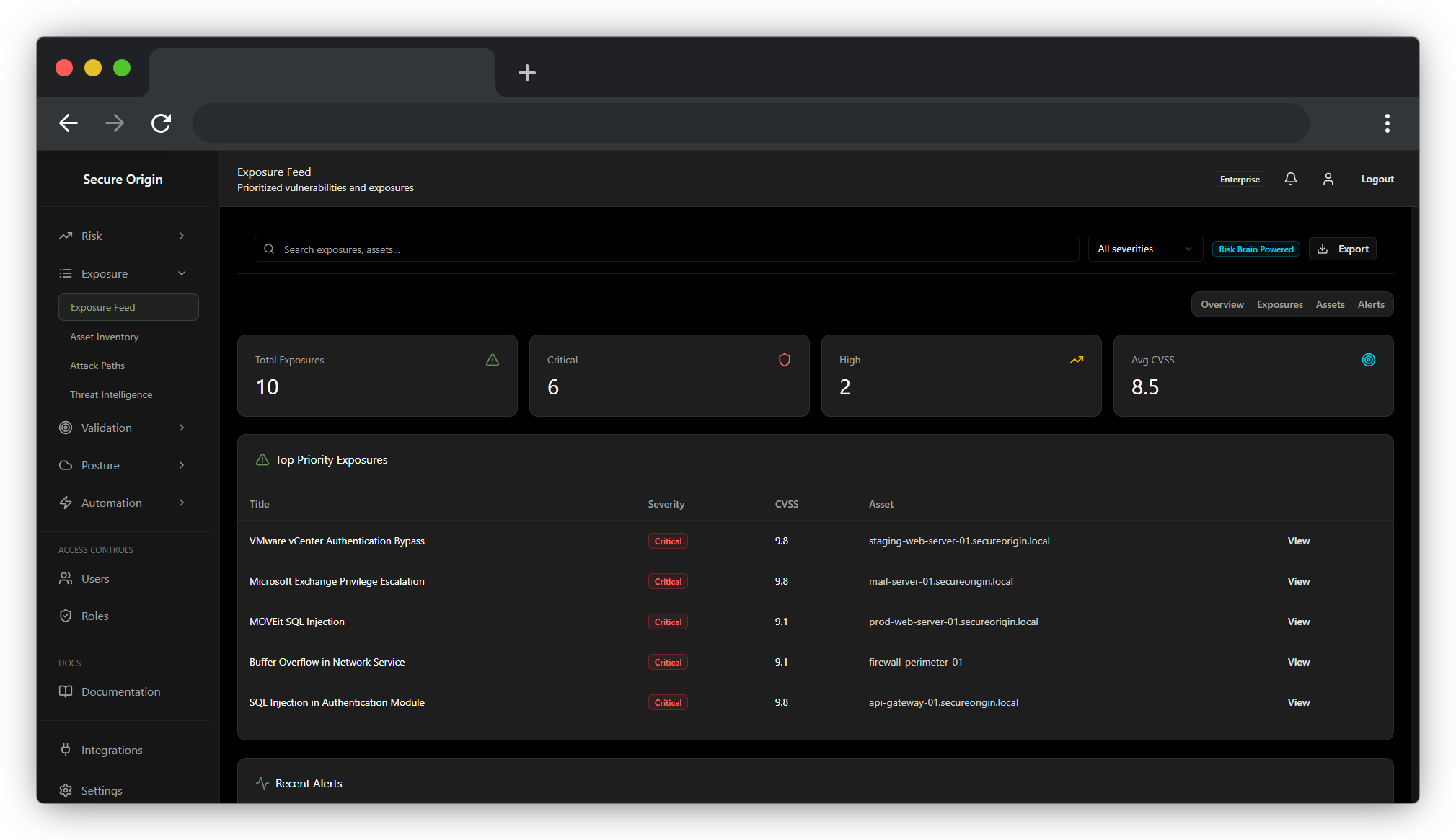
Scoping & Discovery
Unified Visibility Across Your Surface
Establish a reliable asset baseline by continuously cataloging hardware, software, cloud resources, and identity assets. Secure Origin helps teams identify and track their most critical systems—so discovery stays current across the entire attack surface.
.png)
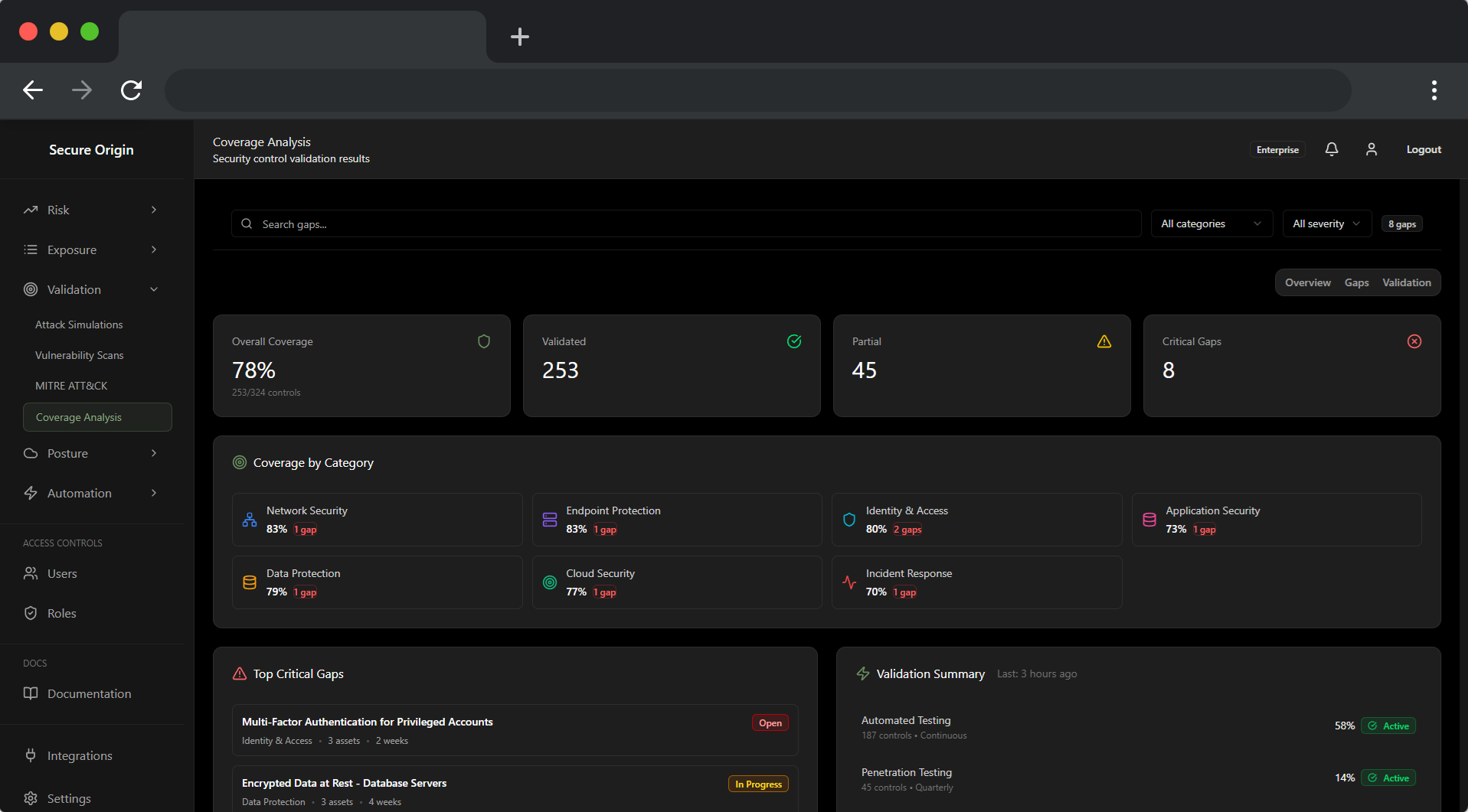
Prioritization
Context-Aware Risk Prioritization
Move beyond generic vulnerability lists. The Risk Brain correlates technical findings with identity posture, asset criticality, and business context to rank risks by real-world impact, not theoretical severity.
Validation
Continuous Control Validation
Stop assuming your controls are effective—start verifying them. Secure Origin uses automated validation techniques to assess detection coverage and identify gaps across existing EDR and SIEM tools, producing measurable insights into control effectiveness over time.
.png)
Mobilization
Automated Response and Containment
Enable faster, consistent response through automated workflows. Secure Origin supports alert enrichment, response orchestration, and containment actions—while maintaining audit-ready logging to support investigations and compliance requirements.
.png)





